Description
Resolution
We have a JPG image available :
I started by taking a quick look at the image content :
curl http://static.wargame.ndh/hellofriend.jpg | more
We note that the end of the image paths appear :
WhoAmI.png Hello_friend/ Hello_friend/0/ Hello_friend/0/64.png Hello_friend/1/ Hello_friend/1/61.png Hello_friend/2/ Hello_friend/2/72.png Hello_friend/3/ Hello_friend/3/6b.png Hello_friend/4/ Hello_friend/4/63.png Hello_friend/5/ Hello_friend/5/30.png Hello_friend/6/ Hello_friend/6/64.png Hello_friend/7/ Hello_friend/7/65.png Hello_friend/8/ Hello_friend/8/IsItReal.jpg
I look at the exact contents using binwalk :
binwalk hellofriend.jpg DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 JPEG image data, JFIF standard 1.01 382 0x17E Copyright string: "Copyright (c) 1998 Hewlett-Packard Company" 3192 0xC78 TIFF image data, big-endian, offset of first image directory: 8 116141 0x1C5AD Zip archive data, at least v2.0 to extract, compressed size: 6264, uncompressed size: 6376, name: WhoAmI.png 122445 0x1DE4D Zip archive data, at least v1.0 to extract, name: Hello_friend/ 122488 0x1DE78 Zip archive data, at least v1.0 to extract, name: Hello_friend/0/ 122533 0x1DEA5 Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/0/64.png 126981 0x1F005 Zip archive data, at least v1.0 to extract, name: Hello_friend/1/ 127026 0x1F032 Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/1/61.png 131474 0x20192 Zip archive data, at least v1.0 to extract, name: Hello_friend/2/ 131519 0x201BF Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/2/72.png 135967 0x2131F Zip archive data, at least v1.0 to extract, name: Hello_friend/3/ 136012 0x2134C Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/3/6b.png 140460 0x224AC Zip archive data, at least v1.0 to extract, name: Hello_friend/4/ 140505 0x224D9 Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/4/63.png 144953 0x23639 Zip archive data, at least v1.0 to extract, name: Hello_friend/5/ 144998 0x23666 Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/5/30.png 149446 0x247C6 Zip archive data, at least v1.0 to extract, name: Hello_friend/6/ 149491 0x247F3 Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/6/64.png 153939 0x25953 Zip archive data, at least v1.0 to extract, name: Hello_friend/7/ 153984 0x25980 Zip archive data, encrypted at least v2.0 to extract, compressed size: 4381, uncompressed size: 4882, name: Hello_friend/7/65.png 158432 0x26AE0 Zip archive data, at least v1.0 to extract, name: Hello_friend/8/ 158477 0x26B0D Zip archive data, encrypted at least v2.0 to extract, compressed size: 101679, uncompressed size: 133658, name: Hello_friend/8/IsItReal.jpg 260229 0x3F885 Zip archive data, at least v1.0 to extract, name: Hello_friend/9/ 260274 0x3F8B2 Zip archive data, encrypted at least v2.0 to extract, compressed size: 286495, uncompressed size: 298687, name: Hello_friend/9/3xploits.jpg 549041 0x860B1 End of Zip archive
It is noted that the image contains a zip file, we try to extract it with the command :
unzip hellofriend.jpg => [hellofriend.jpg] Hello_friend/0/64.png password:
A password is requested.
To find the password had to guess (classic NDH).
Referring to the statement and the name of the image “Hello Friend”, we fall quickly on the TV series “Mr Robot”.
Looking at the Wikipedia page ( https://fr.wikipedia.org/wiki/Mr._Robot_(s%C3%A9rie_t%C3%A9l%C3%A9vis%C3%A9e) ) we quickly find the password for the archive : fsociety
unzip hellofriend.jpg => [hellofriend.jpg] Hello_friend/0/64.png password: fsociety
Once unpacked we get the following tree :
. ├── Hello_friend │ ├── 0 │ │ └── 64.png │ ├── 1 │ │ └── 61.png │ ├── 2 │ │ └── 72.png │ ├── 3 │ │ └── 6b.png │ ├── 4 │ │ └── 63.png │ ├── 5 │ │ └── 30.png │ ├── 6 │ │ └── 64.png │ ├── 7 │ │ └── 65.png │ ├── 8 │ │ └── IsItReal.jpg │ └── 9 │ └── 3xploits.jpg ├── hellofriend.jpg └── WhoAmI.png
Using binwalk us quickly identify an archive in the picture “3xploits.jpg” :
binwalk Hello_friend/9/3xploits.jpg DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 186158 0x2D72E Zip archive data, encrypted at least v2.0 to extract, compressed size: 112361, uncompressed size: 302979, name: d3bug.png 298665 0x48EA9 End of Zip archive
Again the archive is protected with a password.
unzip Hello_friend/9/3xploits.jpg => [Hello_friend/9/3xploits.jpg] d3bug.png password:
The name of png pictures looks like hexadecimal, so we are trying to convert into string :
echo -en '6461726b63306465' | xxd -r -p => darkc0de
So we try to put this value as a password :
unzip Hello_friend/9/3xploits.jpg => [Hello_friend/9/3xploits.jpg] d3bug.png password: darkc0de
The password is incorrect.
A Google search leads to a site “WPA / WPA2 Dictionaries Word List” which is available a dictionary “darkc0de.lst”.
So I downloaded the dictionary.
Then I extract the ZIP file to the bruteforcer with fcrackzip :
binwalk -e Hello_friend/9/3xploits.jpg
Extraction is carried out by binwalk :
. ├── _3xploits.jpg.extracted │ ├── 2D72E.zip │ └── d3bug.png
We now have the ZIP file available after installing fcrackzip (via apt) we can bruteforcer the zip file :
fcrackzip -v -D -u -p ~/CTFs/passwords/darkc0de.lst _3xploits.jpg.extracted/2D72E.zip found file 'd3bug.png', (size cp/uc 112361/302979, flags 9, chk be20) PASSWORD FOUND!!!!: pw == How do you like me now?
We unpack the archive with the pass word “How do you like me now?” :
unzip _3xploits.jpg.extracted/2D72E.zip [_3xploits.jpg.extracted/2D72E.zip] d3bug.png password: How do you like me now?
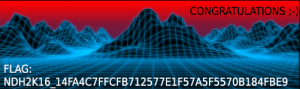
It remains for us to watch the PNG image containing the flag :

 [NDH 2016] [WEB 150 – Hello Friend] Write Up
[NDH 2016] [WEB 150 – Hello Friend] Write Up