Description
Nick’s been eating your grandmother’s strombomi.
Head over to http://nicklesndimes-wq3mhu8l.9447.plumbing.
Gain access to his admin account.
Resolution
We began to check on the Github for the Mellivora CTF engine used by 9447 for security fixes.
https://github.com/Nakiami/mellivora
Moving between commits, fixes etc. but nothing interesting.
Hours later, we decided to reset our account, just for testing purpose.
This is the mail we received:
Password recovery for account PERTE From: No Reply <blackhole@9447.plumbing> Subject: Password recovery for account PERTE PERTE, please follow the link below to reset your password: http://nicklesndimes-wq3mhu8l.9447.plumbing/reset_password?action=choose_password&auth_key=f8ff22e00040028a777e04d926645f42&id=199 Regards, Nick Les' Dimes
As you can see, the auth key is a simple md5.
In the real code, a sha256 hash is generated:
$auth_key = hash('sha256', generate_random_string(128));
Source: https://github.com/Nakiami/mellivora/blob/master/htdocs/actions/reset_password.php#L49
We checked on Google for “f8ff22e00040028a777e04d926645f42“, and we found the plain text was “PERTE“, our test team name 🙂
Next step was to find the email of the admin, but we already had an email of him no?
Remember … “From: No Reply <blackhole@9447.plumbing>” 😉
Entering his email into the reset password page (http://nicklesndimes-wq3mhu8l.9447.plumbing/reset_password) gave us :
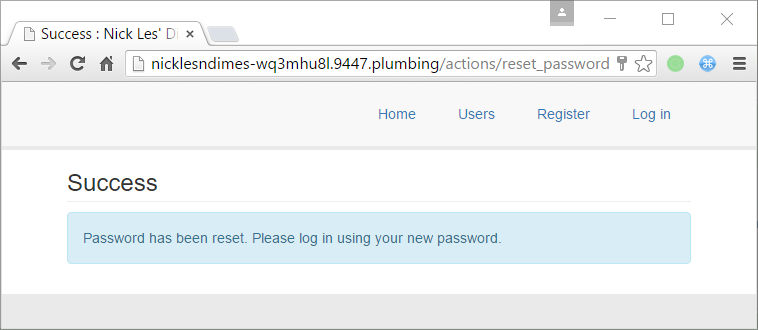
A reset_password has been issued in the DB (as seen : https://github.com/Nakiami/mellivora/blob/master/htdocs/actions/reset_password.php#L51)
It’s time to change the password : the auth_key will be the team name (admin), and the id will be 1.
auth_key plain md5 id 21232f297a57a5a743894a0e4a801fc3 admin 1
The link has to be :
http://nicklesndimes-wq3mhu8l.9447.plumbing/reset_password?action=choose_password&auth_key=21232f297a57a5a743894a0e4a801fc3&id=1
Yeah, it was OK ! We changed the password ! 😀
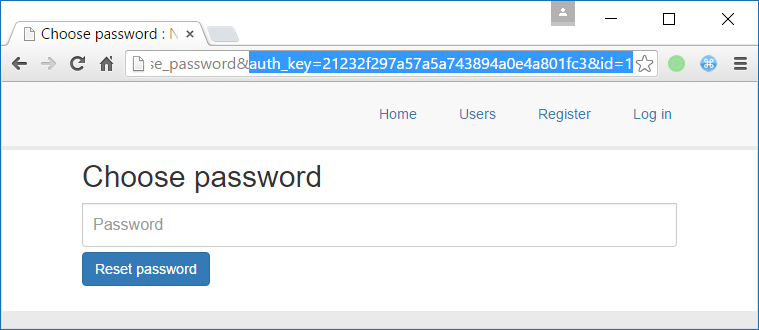
But when we tried… It was wrong 🙁
Probably another team reseted it at the same time. No worries!
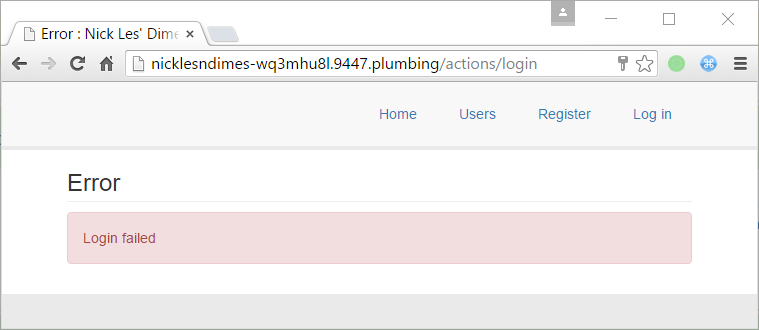
Reseting the password again, we got the following message (WTF is whitelist ?)
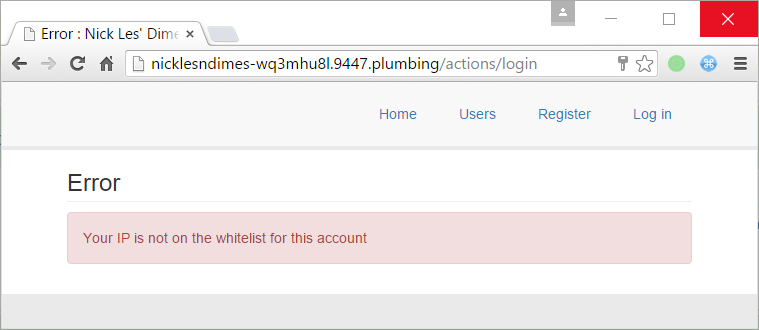
The only thing we can do for “changing” to an allowed IP is to use the X-Forwarded-For header.
Ok, but the IP ? How to find it?
With a DNS request! 🙂
9447.plumbing: 104.28.13.28, 104.28.12.28
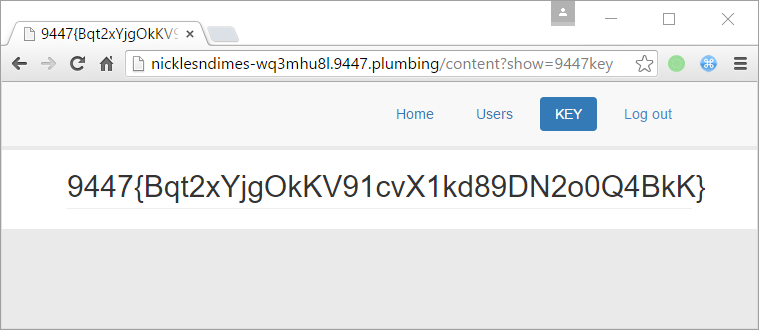
We tried to relog again, and we got the flag! 😉
Flag was : 9447{Bqt2xYjgOkKV91cvX1kd89DN2o0Q4BkK}.
 [9447 CTF 2015] [Web 200 – nicklesndimes] Write Up
[9447 CTF 2015] [Web 200 – nicklesndimes] Write Up
hum. for me the X-Forwarded-For header wasn’t working, had to add the IP to the whitelist.
I found the following code in a .js that was included in the html (http://nicklesndimes-wq3mhu8l.9447.plumbing/js/mellivora.js):
function whitelist_ip(i,t){ $.post("admin/actions/new_ip_whitelist",{action:"new",user_id:i,ip:t}) }It was possible to execute whitelist_ip( 1, YOUR_IP ); from the developer console when logged in with a regular user, then log out / login with admin => works!.
I tried to add my own IP with a XHR request from this JS like you said but was KO for me.
That’s why I finally used this header. 🙂
Maybe someone has later added the IP for 9447.plumbing and I used it!
Thanks for the reply, good to see our ideas are never useless 😀