Description
I’ve forgotten my flag. I remember it has the format “9447{}”, but what could it be?
Unfortunately the program no longer just prints the flag.
flagFinderRedux
Resolution
Using IDA we got the following C disassembly file (it’s just an extract):
while ( memcmp(dest, "9447", 4uLL) )
{
v4 = v8 % (unsigned int)n;
v5 = dest[v8 % (unsigned int)n];
dest[v4] = (unsigned __int64)sub_40060D() ^ v5;
++v8;
}
if ( !memcmp(dest, *(const void **)(v6 + 8), (unsigned int)n) )
printf("The flag is %s\n", *(_QWORD *)(v6 + 8), v6);
else
puts("Try again");
The goal was to hook the second memcmp on GDB, and to check its value.
Offset of the 2nd memcmp was found using objdump:
objdump -D flagFinderRedux-e72e7ac9b16b8f40acd337069f94d524 | grep memcmp
0000000000400500 <memcmp@plt>: 400703: e8 f8 fd ff ff callq 400500 <memcmp@plt> 400729: e8 d2 fd ff ff callq 400500 <memcmp@plt> // <-- we need to set a breakpoint here
Using gdb, we put a breakpoint on 0x400729:
gdb -quiet flagFinderRedux-e72e7ac9b16b8f40acd337069f94d524 Reading symbols from /home/wtf/ctfs/9447/flagFinderRedux-e72e7ac9b16b8f40acd337069f94d524...(no debugging symbols found)...done. gdb-peda$ b *0x400729 Breakpoint 1 at 0x400729
We ran the binary, and got the following output:
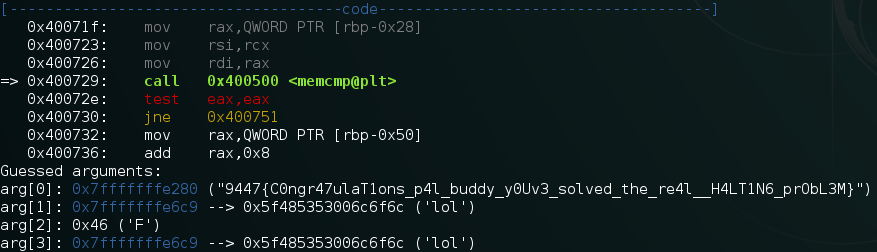
Flag was : 9447{C0ngr47ulaT1ons_p4l_buddy_y0Uv3_solved_the_re4l__H4LT1N6_prObL3M}.
 [9447 CTF 2015] [Reverse 70 – The *real* flag finder] Write Up
[9447 CTF 2015] [Reverse 70 – The *real* flag finder] Write Up