Description
We were given an archive containing a network capture..
Resolution
First, we opened the .pcap file with wireshark.
In seconds we realized the capture contains a multipart downloaded file “flag.zip” : interesting!
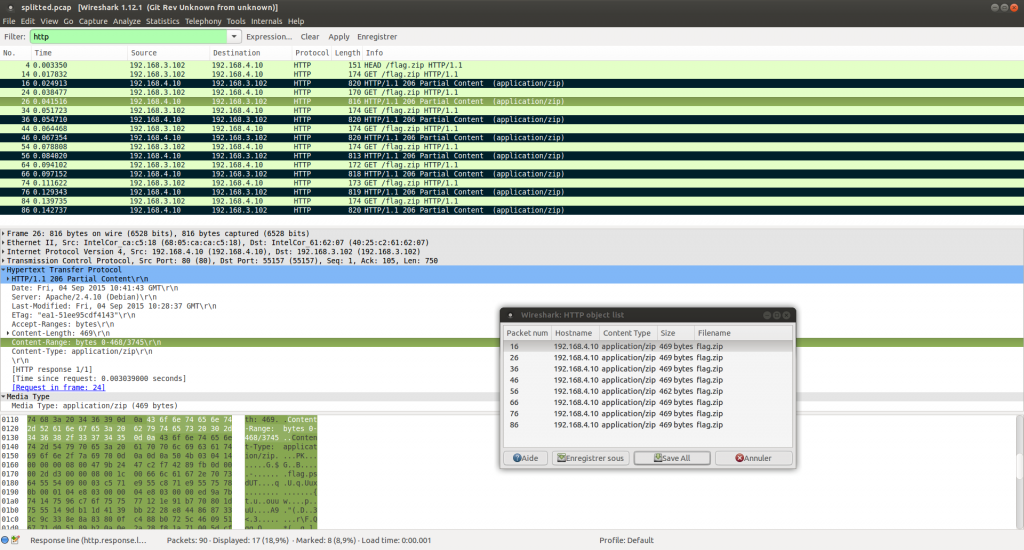 Then we exported all these files, making us 8 parts of zip file.
Then we exported all these files, making us 8 parts of zip file.
Thanks to the HTTP header “Content-Range” we were able to find the order for renaming the extracted .zip files.
| File N | Range | |----------------| | 1 | 0 | | 5 | 469 | | 6 | 938 | | 2 | 1407 | | 7 | 1876 | | 0 | 2345 | | 3 | 2814 | | 4 | 3283 |
Then we renamed the exported files as part-X.zip, following the order of the “Content-Range”.
Finally we assembled the zip archive and extracted it .
$ cat part-*.zip > assembled.zip $ unzip ./assembled.zip
Archive: ./assembled.zip
inflating: flag.psd
$ file flag.psd
flag.psd: Adobe Photoshop Image, 640 x 400, RGB, 3x 8-bit channels
Oh, a psd file ! Let’s see the contents of its layers.
$ convert flag.psd flag.png $ ls *.png
flag-0.png flag-1.png flag-2.png
The extracted layer in the flag-1.png file contains the flag!

 [MMA 2015] [Forensics / Warmup – Splitted] Write up
[MMA 2015] [Forensics / Warmup – Splitted] Write up