Description
Category: Analysis-offensive
Points: 100http://ctfquest.trendmicro.co.jp:8888/95f20bb7856574e91db4402435a87427
Resolution
After creating a test account and log-in, we saw that the website was pretty… useless 🙂 The only thing that changes when we’re connected is that our username is printed. As the website name was “Strange Auth System”, we didn’t check any XSS or SQL injection, which seemed too classical.
After some tests, we saw a weird “bug” happening : randomly, at the logon, we saw that we were connected with other usernames. It means that we were in front of a authentication bug that we could use for stealing accesses. How a bug like that could happen?
We had a little thought, and the most obvious thing is that sessions were overwritten. If we are with someone else’s session, it’s because the session ID created by the server is not unique. Let’s check cookies :
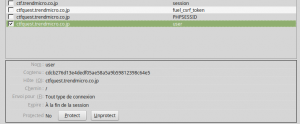
A few tests later, we found the solution. The session cookie is actually a sha1 of the… log-in timestamp. Yep. Do you see the huge thing coming here?
All we have to do is to forge a cookie with a good timestamp, in order to access anyone’s session. But of course we didn’t wanted a random buddy session. No, we wanted the admin session. From here, things became a bit more complicated. We needed to find the good timestamp of the good user. Thanks to the login logs, we rapidly saw that the userID 1 was triggering login connection every single minute. UserID 1? Connection at the exact same second of every minute? Seemed a good target 🙂
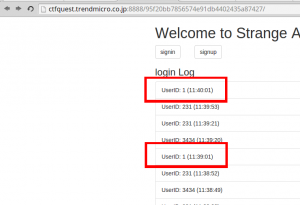
So we created our cookie, with the timestamp corresponding to the admin’s next connection, we loaded it before the admin, and… FAIL!
Oh yes, obviously, we can’t connect to the future. Too bad. By the way, we also can’t connect to the past with on old session cookie.
If we can’t connect neither future or past, we must connect at the right time. It means that we have to connect in the same second that the admin. But as we saw earlier, sessions are overwritten, so we must connect during the same second AND BEFORE the admin connect himself. A sort of race condition if you want. With some tests and a bit of luck, we got the admin session 🙂
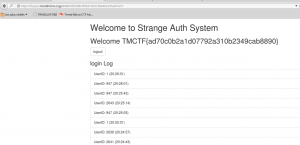
Flag is TMCTF{ad70c0b2a1d07792a310b2349cab8890}
 [Trend Micro 2015] [Analysis-offensive 100] Write-Up
[Trend Micro 2015] [Analysis-offensive 100] Write-Up
You’re really nice 🙂
Thanks buddy 🙂