Description
With a whole scan of 192.168.20.0/24 I found 4 servers.
This is the write-up for the server 192.168.20.10, called “Level 1”.
Resolution
This is an extract of the Nmap scan :
Nmap scan report for 192.168.20.10
Host is up (0.066s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
80/tcp open http
| http-enum:
|_ /phpbb/: Forum
| http-headers:
| Server: Microsoft-IIS/7.0
| X-Powered-By: ASP.NET
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn
445/tcp open netbios-ssn
3306/tcp open mysql MySQL (unauthorized)
3389/tcp open ms-wbt-server Microsoft Terminal Service
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server (R) 2008 Standard 6002 Service Pack 2 (Windows Server (R) 2008 Standard 6.0)
As seen above it’s a Windows server, running :
– a PhpBB forum, available in /phpbb.
– a MySQL server, but we aren’t allowed to connect on.
– a TSE, but we don’t have any credential.
The forum should be the way to get a shell!
After few attempts:
– we can’t register ourselves.
– there was a captcha on the login page.
– exploits for PhpBB 3 needs to be authenticated.
Sometimes I got a SQL error message “Duplicate entry … for key ‘PRIMARY’ [1062]” due to the captcha plugin but nothing more.
What was the next step then? Probably a SQL injection… but where ?
A hint has been given few days after:
ucp.php action parameters.
Ok… let’s see in the source code of the ucp.php page.
https://github.com/phpbb/phpbb/blob/3.1.x/phpBB/ucp.php
I tried several parameters until I got this error message:
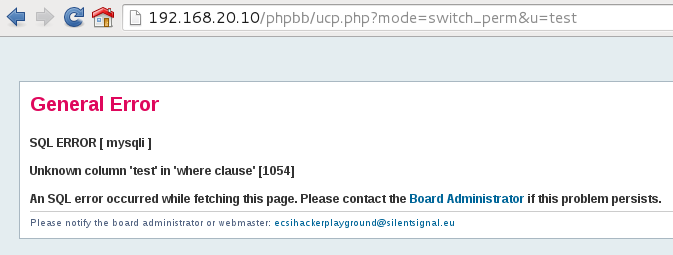
It’s time to exploit it and bypass the error message “HACKING ATTEMPT” when playing with the u parameter. 🙂
The table phpbb471.ecsi_users seems interesting, I selected a few columns :
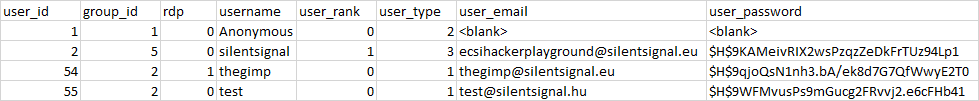
What is the RDP column? A “hint” for TSE allowed users? 🙂
After brute forcing the PhpBB password for user thegimp :
$H$9qjoQsN1nh3.bA/ek8d7G7QfWwyE2T0 | password1
I opened a RDP connection to the server with user “thegimp” and password “password1”.
Then I found the proof file:
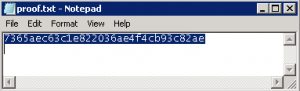
 [eCSI 2015] Level 1 User Write-up
[eCSI 2015] Level 1 User Write-up
Hello dear, how do you brute force & which tools are you used? if it is not secret please share me. i’m also want decrypt it ” $H$9qjoQsN1nh3.bA/ek8d7G7QfWwyE2T0 ” and learn.
Hello Tsuka, sorry for answering late.
You can use oclHashcat with hash-mode 400 and the rockyou.txt dictionnary.
Source: https://hashcat.net/wiki/doku.php?id=example_hashes
(Moreover a hint was given with a link to “Queen – We will rock you” :D)