Description
“You operate in the darkness. Make the world safe… in the shadows.”
firmware-upgrade.pcapng
trojan_firmware.bin
Resolution
Using the network dump we were able to see a dialog between a client (packets in red) and a switch (packets in blue) in TELNET.
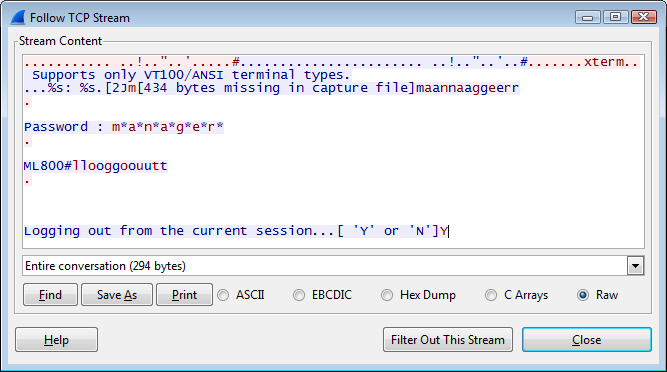 As we can see, the client entered “manager” as login, and the switch output “manager”.
As we can see, the client entered “manager” as login, and the switch output “manager”.
For the password, the client provided “manager” but for each character the switch output an asterisk.
The remaining question was : “What can we do with this login/password ?”… nothing (yet).
We began to reverse the firmware with binwalk…
…until a nmap scan in the 10.0.1.0/24 range revealed something very interesting : a “network switch” administration console 😀
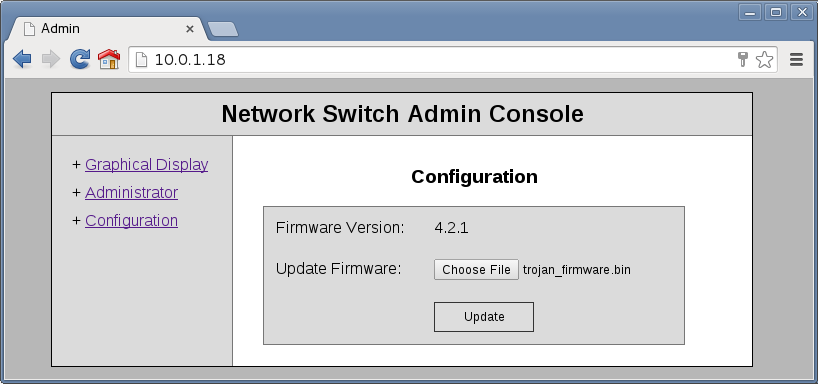
I used the manager:manager credentials to login… and it was OK ! 🙂
Then I selected the firmware update to test, and clicked on the Update button.
Few seconds after, a nice popup shown :
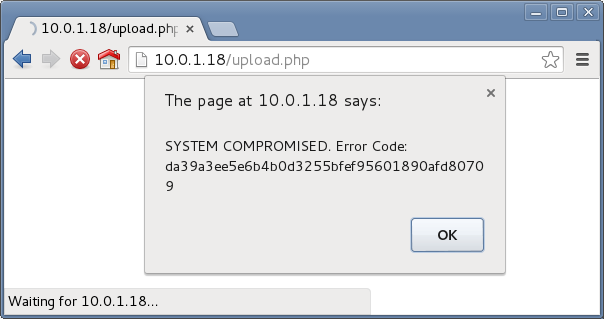
Flag was : da39a3ee5e6b4b0d3255bfef95601890afd80709.
 [MITRE STEM 2015] [Cyberville 500] Write Up
[MITRE STEM 2015] [Cyberville 500] Write Up
Can you feed us with option argumments that used with binwalk
Hello!
As it was useless, I didn’t kept any log for this.
I’m quite sure having used binwalk with the options -e -M.
Maybe the firmware mod kit too!