Description
100Points
Our IT staff captured this weird looking transaction.
Can you tell us what it says??
Download the pcap : ce6e1a612a1da91648306ace0cf7151e6531abc9
Resolution
By opening the pcap file, we can clearly see that there is no useful network capture. Obviously, there is only two types of packets :
- The client, which sends SYN packets to port 19991
- The server, wich replies to the client with RST and ACK flags setted
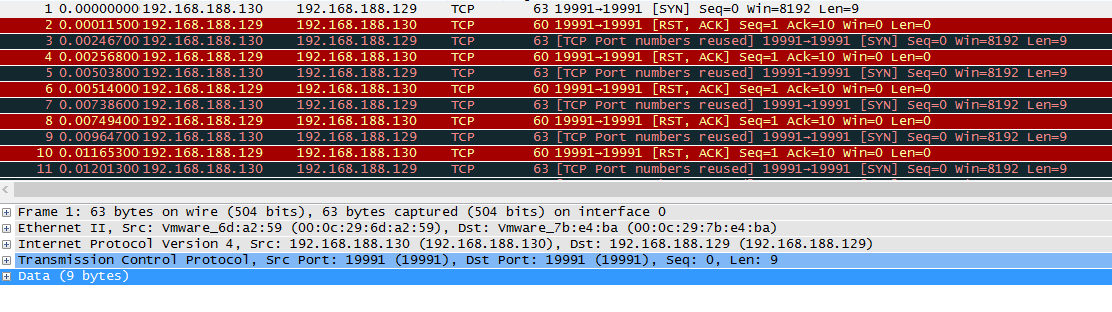
If you know a bit about network, you could clearly see that there is no three way handshake in the pcap, which is (almost) mandatory for any TCP conversation.
Moreover, there is some payload on SYN requests. Sending data in the SYN packet seems to be RFC compliant, but is really unusual and weird (except for the TCP Fast Open, as previously said)
Why not take a look at the payloads on the client packets ?
By checking the firsts packets, we can see that :
- every packet data is beginning with the “GOAT\x01” string
- the size is always 9 bytes long
- after the initial “GOAT\x01”, there is the useful payload.
For example, the two firsts SYN packets are as this :
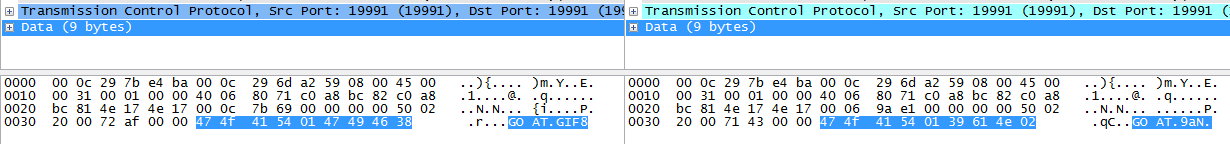
By removing the “GOAT\x01” on both payloads, we clearly see the gif magic bytes “GIF89a”. There is a picture inside the packets.
As far as we know, there is no option on wireshark to export payload from SYN, so we wrote a little (and really ugly) python script to extract the datas. It symply works by looking at every “GOAT\x01” strings and extracting the 4 next bytes. Once the pcap is analysed, the script creates a file with the extracted values.
#!/usr/bin/python3
# -*- coding: utf-8 -*-
import sys
import time
import os
h = open('chall.pcapng', 'rb')
s = h.read()
end = 0
deb = 0
found = b''
while end is 0:
if s.find(b'GOAT', deb) is not -1:
tmp = s.find(b'GOAT', deb)
found = found+s[tmp+5:tmp+9]
deb = tmp+1
else:
end = 1
h2 = open('res.gif', 'wb')
h2.write(found)
h2.close()
h.close()
We opened the resulting gif and saw the flag on one of the frame (I don’t know why, but wordpress seems to have issues to load gifs, click here if the image don’t appears).
In order to have only the good frame, we opened the gif with gimp and hid the useless frames to have the flag.
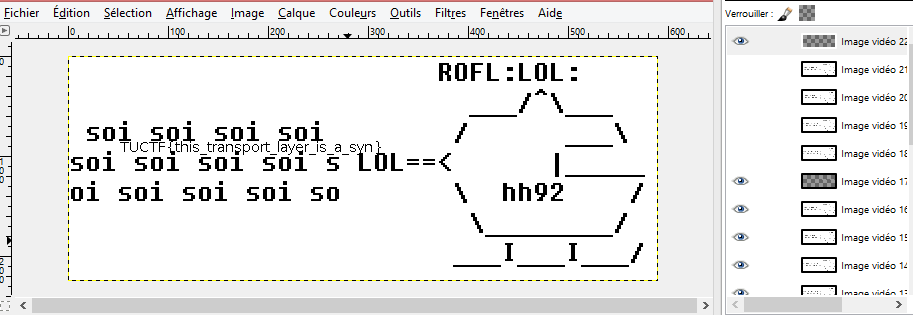
The flag was TUCTF{this_transport_layer_is_syn}
 [TUCTF 2016] [Misc 100 – The Nack] Write Up
[TUCTF 2016] [Misc 100 – The Nack] Write Up