Description
No Big Deal
50 points / Solved 214 times
Sometimes the answer is immediately obvious, sometimes it’s obscured.Find the answer in here
Resolution
Funny thing about that challenge is that we found the flag of the part 2 and spent a little more time findind out the flag of the first part.
You need to take the hint into account: sometimes it’s obscured.
Running strings and other tool isn’t really usefull taking into account that the pcap given is pretty heavy.
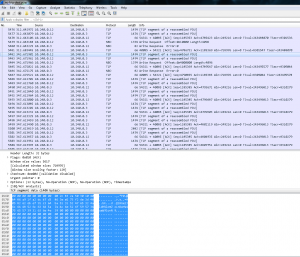
We can see that the network capture has different time transfer, so I took a look at the packets beginning at each time line and at the end to see if there was anything suspicious.
At 342 seconds, we can see a packet with some printable characters.
It looks like base64, so we give it a try:
laxa:_no-big-deal.pcap.extracted:12:33:29$ strings q.bin
_BHRfS_M
Q1RGe2JldHRlcmZzLnRoYW4ueW91cnN9
laxa:_no-big-deal.pcap.extracted:12:33:33$ echo -n 'Q1RGe2JldHRlcmZzLnRoYW4ueW91cnN9' | base64 -d
CTF{betterfs.than.yours}laxa:_no-big-deal.pcap.extracted:12:33:40$
Flag is: CTF{betterfs.than.yours}
 [Google Capture The Flag 2016] [Forensics 50 – No Big Deal] Write Up
[Google Capture The Flag 2016] [Forensics 50 – No Big Deal] Write Up