Description
Find the Flag!!
Resolution
We are given an apk file which contain an android app, we go there http://www.decompileandroid.com/ and unpack the given apk.
We find 2 interesting files in the src folder:
- a.java
- MainActivity.java
By studying those sources, we quickly understand how the application is working, it’s pretty simple, we have a text field and a button, when clicking on the button, the application verify it’s state and if it’s correct, gives us the flag.
We also see that the application is using a dynamic library that we find in the lib folder: libadjni.so.
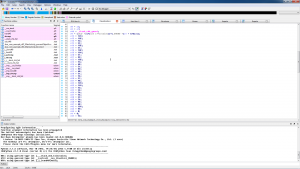
The library is an ARM 32bit lib, hopefully, IDA can decompile this and help us! Most of the functions are not really interesting, but we find this:
The application is comparing the given input to this, so we transform it into an ASCII string which gives us: ef57f3fe3cf603c03890ee588878c0ec
And then, we enter this into the application to get the flag:
Flag is: 833489ef285e6fa80690099efc5d9c9d
 [Sharif University CTF 2016] [Reverse 100 – Android App] Write Up
[Sharif University CTF 2016] [Reverse 100 – Android App] Write Up