Description
Title : Blocked
Resolution
The application is quite simple. We can register and login.
After the login, a message says that our account hasn’t been found or is locked.
So, we could guess that the goal is to find a way to access an unlocked account.
It’s easy to find an unlocked account, as almost every website on earth has an “admin” user ^^
After some tests, we could easily guess that the vulnerability is a matter of SQL.
Classical SQL injections didn’t worked, unfortunately but there is others MySQL flaws.
One of them is MySQL Truncation, a really funny one.
The concept is to play with the size of the sent datas.
In short, if we send a string longer than the DB entry could accept, MySQL will return that the entry doesn’t exists.
So if we create an “admin -with a lot of spaces- x” account, MySQL will says that the entry doesn’t exists AND the PHP application will think that it’s OK to create the account.
After that, the DB will insert it, but as the entry is too long, Mysql will truncate it, in order to be as short as it should be.
At this step, we now have two accounts :
- “admin”
- “admin -lot of spaces- “
At last, when we want to connect with our long admin account, the SELECT query will automatically trim our string (as it’s a MySQL feature).
We just have to use our fake admin account, and the application will log us as admin.
You’ll find more information about this flaw here.
Now that this flaw has been explained, let’s try it !
As said before, we need to register with a really long string, as show below.
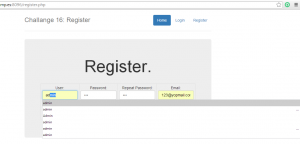
The registration was succesful.
We just have to log in, in order to see if we are correct about this vulnerability.
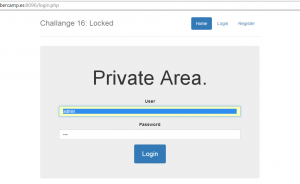
And here we are ! We’re connected with an admin account.
Of course this is not the real admin, but with poorly written code checking authorization only with usernames could be tricked like this !
Here is the flag !
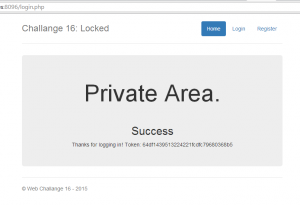
Don’t forget this trick, it could be useful 😉
Enjoy
The lsd
 [Cybercamp 2015] [Web 16 – Locked] Write Up
[Cybercamp 2015] [Web 16 – Locked] Write Up