Description
HARD INTERVIEW
50 Points – SOLVED
interview.polictf.it:80
It wasn’t really a challenge, but as we solved it, we have to do a write up 🙂
As usual, we have to connect to the server. We simply get a prompt, so the first thing to do is trying some commands like ls or pwd, but they aren’t recognised. Just writing “help” gives us some information :
fish@sword:~$ help
A very hard interview: Codename Blow…Fish
Maybe you can help me with something…
DOD d-base, 128 bit encryption….What do you think?
Maybe slide in a Trojan horse hiding a worm…
I have been told that best “crackers” in the world can do it 60 minutes, unfortunately i need someone who can do it in 60 seconds… naturally with the right incentives 😉
If you know what I mean, tell me how a real cracker accesses to a remote super protected server…Possible commands:
hacker: Write code as a real hacker
help: Give informations about the program
hint: Gives a little hint
exit: Loser…bye Bye
ssh: A tiny ssh command
date: A very useful and innovative feature
the hacker command is just a troll, after typing it, the shell sends us some code, just, you know, to “code like a real hacker”
fish@sword:~$ hacker
#include <linux/signal.h>
#include <linux/personality.h>
struct rt_sigframe {
/* 00:29:57 */
err = __copy_to_user(&(sf->uc.uc_mcontext.regs), regs,
err = __copy_from_user(&set, &sf->uc.uc_sigmask, sizeof(set));SYSCALL_DEFINE0(rt_sigreturn)
current_thread_info()->restart_block.fn = do_no_restart_syscall;
[and so on]
The date command gives us the date (you didn’t see that coming, no? 🙂 ) and the exit command, well… just exit the shell and closes the connection.
So there is only two commands remaining : hint, and ssh. Just let’s begin with hint:
fish@sword:~$ hint
usage: ssh username@address
username: THE username
address: a not so easily reachable IP address
Very simple…isn’t it?
OK, it’s a bit obvious, we have to use the ssh command with THE username and a not so easily reachable IP address. Hmmm, I guess we could try root@127.0.0.1 !
fish@sword:~$ ssh root@127.0.0.1
… Username not found
… Address not reachable
NOP ! Maybe we could try another classic username :
fish@sword:~$ ssh admin@127.0.0.1
… Username found
… Address not reachable
Yes ! We got it, now we just have to find the IP.
Hmmm, the hint told us about a “not so easily” reachable IP… Hey! Did you read the quote from the help command?! No ? OK, I’ll put here :
A very hard interview: Codename Blow…Fish
Maybe you can help me with something…
DOD d-base, 128 bit encryption….What do you think?
Maybe slide in a Trojan horse hiding a worm…
I have been told that best “crackers” in the world can do it 60 minutes, unfortunately i need someone who can do it in 60 seconds… naturally with the right incentives 😉
If you know what I mean, tell me how a real cracker accesses to a remote super protected server…
Yup. The swordfish movie. And we ALL know that every “hacking” scene in the movies are so fake that they always shows us IP addresses that are… “not so easily reachable”! Why not try to look at the scene? https://youtu.be/zfy5dFhw3ik?t=1m36s (you’ll have to slow the video down or play/pause multiple times, beacause the picture stays for a really short time)
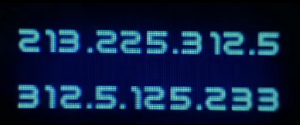
What what what? Is it… a… not so reachable IP address? Let’s try it!
ssh admin@312.5.125.233
flag{H4ll3_B3rry’s_t0pl3ss_sc3n3_w4s_4ls0_n0t4bl3}
Here is the flag : flag{H4ll3_B3rry’s_t0pl3ss_sc3n3_w4s_4ls0_n0t4bl3}
Oh, and btw, a topless scene? I must watch this movie again 🙂
Enjoy
The lsd
 [PoliCTF 2015] [Grabbag50 – Hard Interview] Write Up
[PoliCTF 2015] [Grabbag50 – Hard Interview] Write Up