Description :
Le fichier
pcapsuivant contient une capture réseau d’un transfert via le protocole SMB2. Il s’agit de retrouver un fichier zippé qui transité sur le réseau et d’en extraire la clef qu’il contient.
So, the goal of this network challenge is to find a zipped file transferred over the network. As the description said, the transfer has been made via SMB2 protocol. As usual, we first have to open the pcapng file with wireshark.
Once the file is checked and OK, we now have to extract files transfered via SMB2 protocol. We could try with Network Miner, as for the net1. Unfortunately, this soft can’t handle SMB2 files (moreover, it can’t open pcapng files in the free edition, no matter, save as pcap on wireshark and it’s ok ;)).
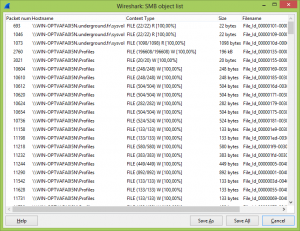
In order to get the files, we will use wireshark which has an SMB/SMB2 extract option in the File > Export Objects menu
Once the extract is over, we have a lot of files (about 400). The question is : “how to get the good one ?” The answer is quite easy, the “file” command under linux. With a few lines of bash, we can get the type of each file :
for f in /home/synsynhack/ do file $f; >> /home/synsynhack/smb/filetypes done
A quick view on the resulting file (/home/synsynhack/smb/filetypes) let us know where the zip file is.
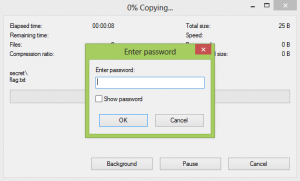
We just have to open it aaaaaaaand… password secured !
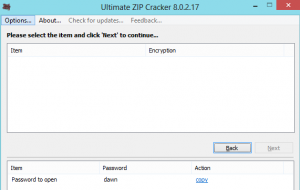
As I don’t have on my computer any zip password cracker, I downloaded Ultimate Zip Password, in order to brute force the pass.
Meanwhile, I looked every files transfered via SMB, in case of the password can’t be bruteforced in a reasonnable time (watching 400 files in a row could be very annoying, trust me !) No pass in the other files, but in the mean time, Ultimate Zip Password broke the pass. The last step was to open the flag file to see this text :
Le flag est : AsHTwn1xw2
Enjoy
The lsd
 [HackingWeek 2015] [Net3] Write Up
[HackingWeek 2015] [Net3] Write Up