Description :
Le fichier pcap suivant contient une capture réseau d’une connexion FTP. La clef de ce challenge est contenu dans l’un des fichiers transférés pendant cette connexion FTP.
For this first network challenge, a pcap file was given. The goal was to find the flag, contained in a file transferred with the FTP protocol
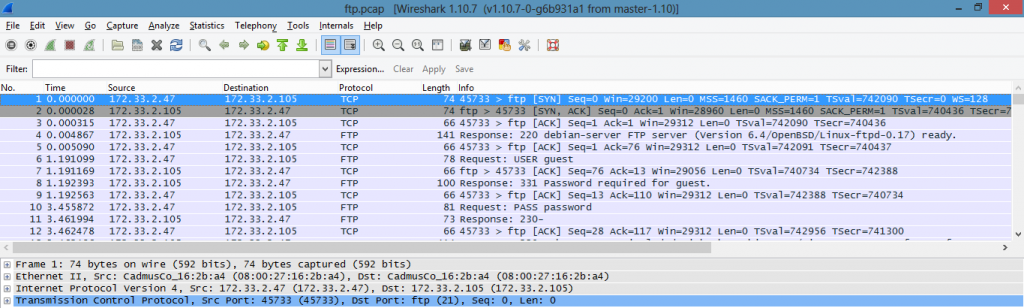
The first step was to open the file with wireshark, in order to see the integrity of the file and packets.
The second step was to find the file. As wireshark have some file extraction capabilities, I checked on google in order to find how to get FTP file from a pcap. Unfortunately, there is no built in function to get files from FTP, as we can see on this link : https://shankaraman.wordpress.com/tag/how-to-extract-ftp-files-from-wireshark-packet/. The method is manual and prone to errors (and I’m lazy too :))
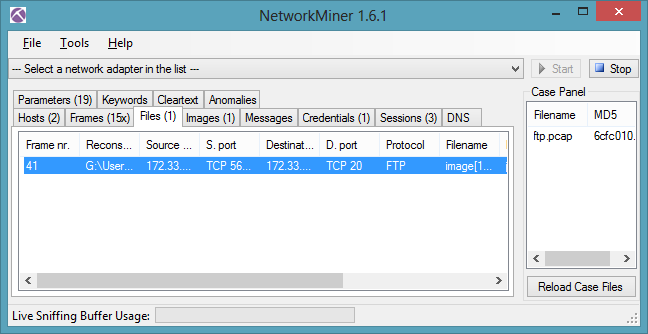
So I looked for another soft to do this, and Network Miner (http://sourceforge.net/projects/networkminer/)came to my google results, we can load a pcap and it will show us files seen from different protocols as HTTP, or FTP in our case :). Once the pcap was loaded, the flag file has been found by the soft and voilà !
Enjoy
The lsd
Links :
other method : using only Wireshark http://wikiufox.no-ip.org/doku.php?id=writeup:hackingweek2015:net1
 [HackingWeek 2015] [Net1] Write Up
[HackingWeek 2015] [Net1] Write Up