Description :
Le fichier
pcapsuivant contient une capture réseau d’un scannmap, retrouvez les services qui ont été trouvés sur la machine cible. La clef de validation seraservice1:service2:service3:...en mettant les services par ordre de ports croissants.
The goal of this challenge was to detect open services on a computer. The given pcap file was a network trace of a nmap scan. As for the net1 chall, the first thing to do is to open the pcap with wireshark, in order to see the data.
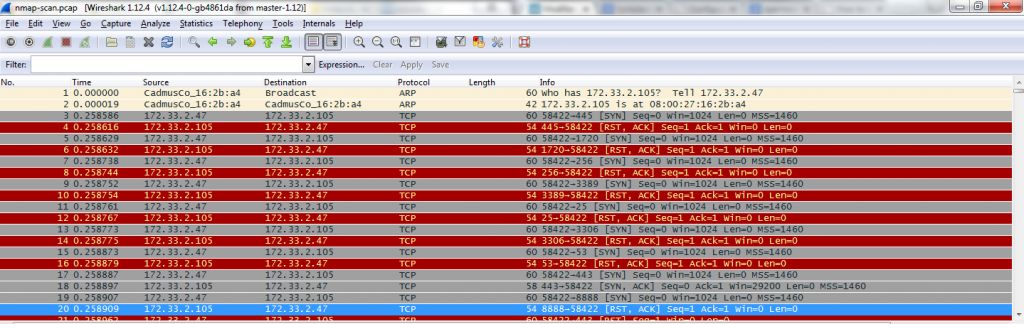
As we can see, the pcap has already been filtered in order to keep only packets about the nmap’ed computer (it begins with an ARP WHO-HAS and we can see only 2 IP source and destination in the firsts packets, which is clearly not a real situation :)). To be sure, let’s go to the statistics menu, in order to check if there are other IP addresses.
OK, as we are now sure that there is only interesting flows, how can we get open ports ? The answer is quite easy : when a service is listening on a computer, there is a three way handshake at TCP level (syn/syn ack/ack – see my name, got the reference ? 🙂 -)
- The first one from the source
- The second from the destination
- The last one from the source again.
In a normal situation, once the three way handshake is over, data could be transferred over . As it’s a nmap scan, there is a little difference, the third packet contains an ACK and an RST flag, in order to drop the connection, but there is no issue with that for this challenge.
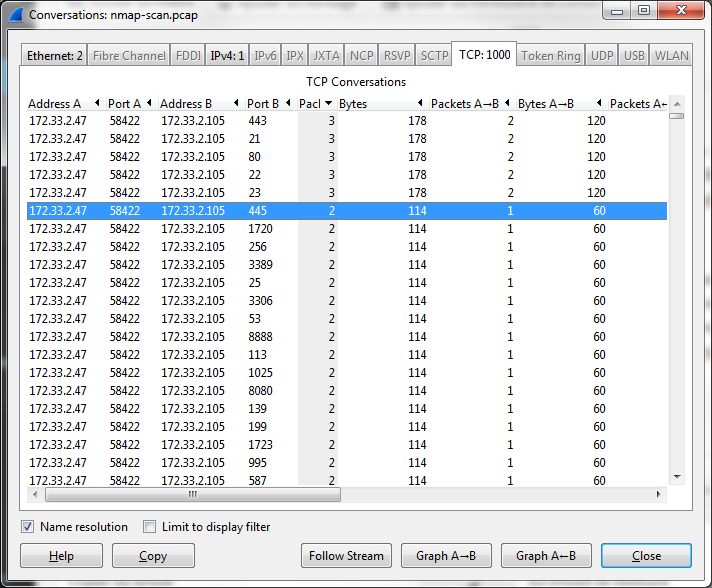
So, if you’re still with me, for any open port, we’ll have three packets, and for closed ports we’ll have one or two packets (only SYN, or SYN/RST). Let’s go to the statistics menu again :
As you can see, there are five conversations with three packets on the following ports : 443, 21, 80, 22, 23 which are HTTPS, FTP, HTTP, SSH and telnet.
Let’s try this flag ftp:ssh:telnet:http:https
And here we are, one more flag !
Enjoy
The lsd
Links
Other method : using a Wireshark filter : http://wikiufox.no-ip.org/doku.php?id=writeup:hackingweek2015:net2
Three way handshake : https://en.wikipedia.org/wiki/Handshaking
 [HackingWeek 2015] [Net2] Write Up
[HackingWeek 2015] [Net2] Write Up