Description
The goal was to bypass the firewall, the target os 10.2.63.250 and you can scan it. (sorry, not the real description, but we forgot to backup it.).
Resolution
Yes, it’s been a while since the last Write Up we wrote. Too much time obviously. That’s why we are going to fix that mistake with this blog post 🙂
So, a few days ago, there was the DefCamp finals and as we were in the top15 in the quals, we went onsite to beat challenges !
One of them was Infinity, a web one. So let’s do it 🙂
As explained in the description, we were allowed to scan the IP. This is quite unusual, so we decided to have a look.
The first thing to do is to run nmap (actually zenmap) ant to run an intense scan onto the IP 10.2.63.250. Here are the results:
PORT STATE SERVICE VERSION
8008/tcp open http
8010/tcp open ssl/http-proxy FortiGate Web Filtering Service
8020/tcp open unknown
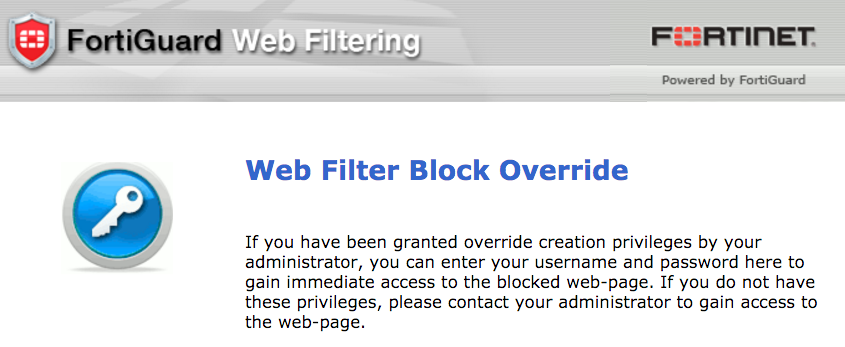
OK. So, three open ports. By connecting onto them with a browser we can see that TCP/8008 redirects to TCP/8010 and show us this webpage.
OK. A fortigate proxy. Seems weird, because it’s really unusual to have challenges with manufacturer appliances to pwn. But, ok, anyway.
After some tests, we can see that the TCP/8020 is the proxy port, and setting it on a browser blocks the navigation, and shows us the same webpage as explained before
So, to sum up, we got 3 ports on an appliance, that seems hard to exploit. But hey, it’s a CTF, there should be some vulnerability 🙂
We tried almost everything to bypass the proxy, like :
– trying to connect to localhost with the proxy
– scanning every ports on the 10.2.63.250 with the proxy
– scanning every IP on the 10.2.63.0/24 subnet
We even tought to do some vlan hopping attacks (which seems very weird because it’s a web challenge).
We also began to scan for UDP open ports, but, as you may know UDP scan is sooooooo long. As there was at least 18h of scan, we aborted it.
In the mean time, as nobody validated the challenge, the organizers gave hints like “Are you sure that you scanned every TCP/UDP ports ?” and “I’m ABSOLUTELY sure that there is only ONE open port”.
At this time, we were like “Whaaaaaaat?! We can see at least 3 ports! What the hell”
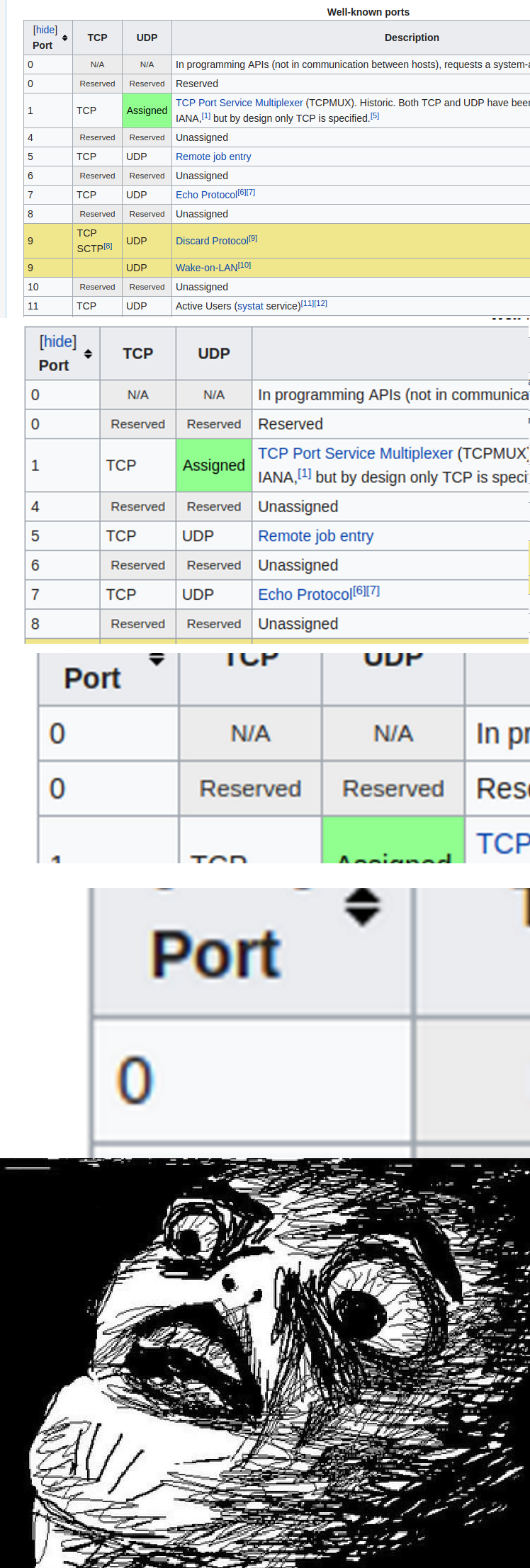
After a while, the last hint gave us the answer : “Have you tested EVERY ports : https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers”. Ok buddy, let’s see the wiki page… We opened it and…
THE PORT 0 ! This DUMB nmap didn’t scanned explicitly for this port ! Go !
wget 10.2.63.250:0
DCTF{a2c41d9a5c14e53863efe7b0af8783d8e697f5717f26adcd34b10b932cd9cc32}
WHAT THE…! OK nmap, we hate you to not try this port.
So, to sum up, the trick was pretty fun, but we tought that every one had lost their mind with the fortigate web filter as we did. Moreover, the hint saying that there was only one open port should also drove everyone mad, and the category should have been Misc since there was no web at all.
So, flag was DCTF{a2c41d9a5c14e53863efe7b0af8783d8e697f5717f26adcd34b10b932cd9cc32}.
(Oh, and we first blooded it \o/)
 [DCTF Finals 2017] [WEB 400 – Infinity] Write Up
[DCTF Finals 2017] [WEB 400 – Infinity] Write Up