Description
Although it is easy, but I still made this challenge because it is useful in penetration testing.
This challenge doesn’t allow DIRBUSTER or other SCANNER.
Resolution
This challenge was quite easy, nevertheless, it was funny because we never saw this before during CTF. Moreover the “Only true pentesters will find it” challenged us 🙂
So, by landing on the website, we only had a message, as you can see below. We tried some classic things (robots.txt, common directories, etc.) but it was obviously useless.
After a few minutes, something popped on our minds : “WHO on earth can do an SSL configuration for a website which has absolutely no need for SSL?”. Yes, the answer is no one.
So, if there is a certificate on this website, there must be a reason. Let’s check it.
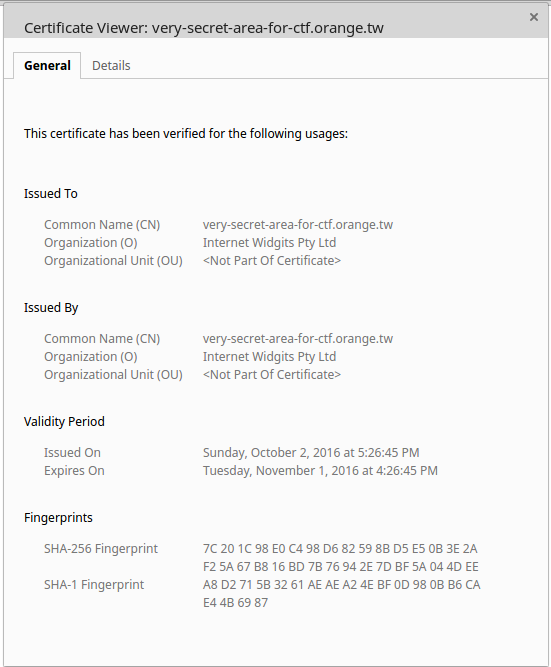
As you can see on the screenshot, the certificate is attributed to “very-secret-area-for-ctf.orange.tw”. Wohhh, too easy buddy ! Just have to load this website and… Massive failure. No DNS resolution… Just to be sure, we tried to nslookup, but we already knew that the NS answer would be negative.
So now what ? We have a non working domain name, and the challenge server.
Oh wait. We have a domain name… We have a challenge server… Why not try to bind them?
Actually, the DNS protocol had been created (partially) in order to not have a huge hosts file.
Let’s have a try, we modified our hosts file in order to get the very-secret-area-for-ctf.orange.tw pointing to the challenge server (see the screenshot).
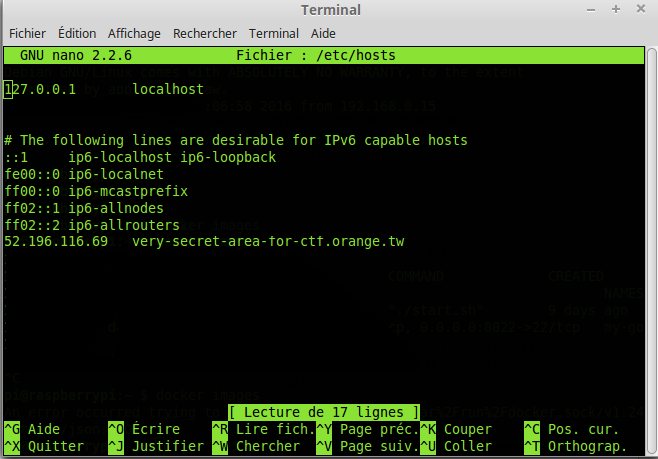
If everything works, we just have to load the website and see what’s going on.
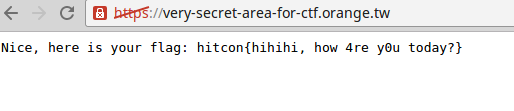
BINGO! There was an apache vhost listening only for this domain name 🙂
100 points for 5 minutes of tests, not bad !
Flag was hitcon{hihihi, how 4re y0u today?}
 [Hitcon 2016] [WEB 100 – %%%] Write Up
[Hitcon 2016] [WEB 100 – %%%] Write Up