Description
Recover the flag from this session
Attachment: misc50.zip
Resolution
The challenge is giving us only a pcap file. As it’s the first Misc challenge, it seemed to be quite easy. The first thing to do with a pcap is to check used protocols :
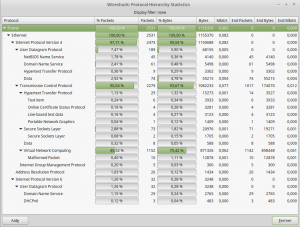
Hmmm Netbios, HTTP(S), DNS, and VNC, quite classical. Usually, flags could be found on HTTP (by giving us next steps for example), but nothing here. The only weird thing was a css.php file, but it wasn’t useful for the challenge. DNS, Netbios, and HTTPS weren’t useful neither.
So, we took what was remaining: VNC. After some search, we found the chaosreader tool, which can extract the VNC packets, create a python script that can replay the VNC session. But… It failed 🙁
We searched some others toosl, to crack the VNC pass, but hey, it’s a 50 points challenge. It should be easier than that!
After looking directly the pcap, we saw something…
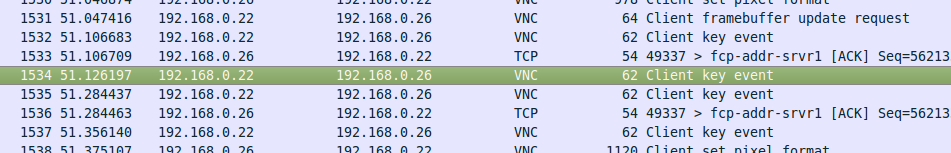
Wait, what? “Client Key event”? Like “Hey, I’m the client, i’m sending you THIS key”?
Let’s filter on this message type ans see what we could have, with this filter :
(vnc.client_message_type == 4) && (vnc.key_down == 1)
To check if we are good, we just have to look at the packets details :
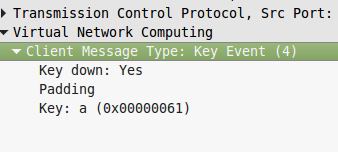
After checking every packet, we can extract this text :
notepad<enter>
can you see me//<bkspace><bkspace><shift L (multiple time)>_<bkspace>
<enter(multiple time)>
EKO{NOT_anym0re_VNC_hax}
YES! WE CAN SEE YOU!
Flag was EKO{NOT_anym0re_VNC_hax}
Enjoy
The lsd
 [EKOParty Part 2 – 2015] [Misc50 – Olive] Write Up
[EKOParty Part 2 – 2015] [Misc50 – Olive] Write Up