Description :
Nos han enviado un archivo para su reconstrucción. Del archivo conocemos lo siguiente:
Se trata de parte de un fichero comprimido del que se ha perdido la cabecera de, exactamente, 10 bytes. cabecera
Se sabe que contiene un fichero de texto ASCII.
La cabecera no tiene ningún un campo opcional.
El segundo byte de la cabecera perdida es 0x8B.
El fichero se generó en una máquina UNIX.
I’m not what we could call a killer in reversing, but this challenge wasn’t about ASM ans stuff like that, so I tried, (and succeded) it.
Translated in english, the description is :
“A archive file was given in order to reconstruct it. We know this about it :
- The compromised file “lost” only the header, exactly 10 bytes
- We know that it’s an ASCII text file
- the header doesn’t have any optional field
- The second byte of the “lost” part is 0x8B
- The file has been generated on a UNIX computer
With this description, we have everything in order to reconstruct the file.
At first we need two things : this is an archive file, and the second byte is 0x8B. As you know, almost any files have a magic number, in order to know the file type. This magic number is usually two or three bytes, at the very beginning of the file.
As the description give us the second byte, we must check if some archive file types have a magic number XX8B. Following this link, we learn that the gzip type’s magic number is 1F8B.
If we are correct, we already have two bytes.
Following this, we need to reconstruct the 8 remaning bytes, by looking at the file structure, with this link for example.
0 2 bytes magic header 0x1f, 0x8b (\037 \213)
2 1 byte compression method
0: store (copied)
1: compress
2: pack
3: lzh
4..7: reserved
8: deflate
3 1 byte flags
bit 0 set: file probably ascii text
bit 1 set: continuation of multi-part gzip file, part number present
bit 2 set: extra field present
bit 3 set: original file name present
bit 4 set: file comment present
bit 5 set: file is encrypted, encryption header present
bit 6,7: reserved
4 4 bytes file modification time in Unix format
8 1 byte extra flags (depend on compression method)
9 1 byte OS type
With these informations, we could try to guess the 8 bytes. The third one is used for the compression methode : deflate is probably the most used (actually, I don’t really know, but hey, we have to guess a bit ^^)
The fourth byte contains bit flags. As I didn’t really knew if some flags were used, I tried with 00 in order to try. After all, possibilities were not huge and I could have brute forced it if needed 🙂
The bytes 5-8 were used for timestamps. Do we really need this information ? I guess not 🙂 So I filled it with 11 22 33 44
The 9th byte was useful for extra flags. As the descripton said, there is no optionnal filed. 00 again !
And the last byte was the OS type, which was given in the description : UNIX, which is 03 (following my previous link.
So, to sum up, my ten bytes are these ones : 1f 8b 08 00 11 22 33 44 00 03. To see if I’m right, we just need to add it at the beginning of the file they gave us.
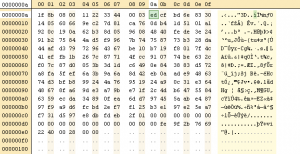
And to try to open it with 7zip.
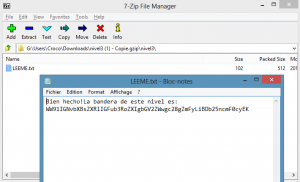
And here is the base64 decoded flag : “You complete another level so far. Congrats!”
Actually, the third byte, with the bit flags is clearly wrong. The description said that the archive is ASCII text, so it shouldn’t be 00, but it seems that 7zip is lazy with the headers 🙂
Enjoy
The lsd
Original file (zipped) : nivel3
 [Cybercamp 2015] [Reverse 3] Write Up
[Cybercamp 2015] [Reverse 3] Write Up