Introduction
The supplied memory image was captured on a compromised machine, analyze it to answer questions (this is the same image for the four forensic tests, useless to download several times).
When the machine was compromised, the attacker installed a Command & Control software that is currently inactive but must contact a server to receive his orders.
Find the server name and the port on which the malware should connect.
The validation key is servername:portnumber.dump.gz (md5sum:1273931ce359f59bce95ce4507e1f4bf)
Resolution
We already know the memory image is a Windows 7 SP1 32 bits, so we use the pstree command to check running processes.
$ python vol.py -f dump --profile=Win7SP1x86 pstree
Name Pid PPid Thds Hnds Time
-------------------------------------------------- ------ ------ ------ ------ ----
0x84c29d40:csrss.exe 320 312 9 340 2015-03-06 08:25:03 UTC+0000
0x8584cd40:wininit.exe 368 312 3 74 2015-03-06 08:25:04 UTC+0000
. 0x85996758:services.exe 464 368 7 202 2015-03-06 08:25:06 UTC+0000
.. 0x83fa9030:taskhost.exe 1024 464 10 208 2015-03-06 08:32:46 UTC+0000
.. 0x85a35030:svchost.exe 576 464 10 353 2015-03-06 08:25:09 UTC+0000
.. 0x83e65190:taskhost.exe 3692 464 5 90 2015-03-06 08:46:23 UTC+0000
.. 0x856edd40:svchost.exe 780 464 19 511 2015-03-06 08:25:11 UTC+0000
... 0x83fd1d40:dwm.exe 1568 780 3 83 2015-03-06 08:32:47 UTC+0000
... 0x83e70a00:dwm.exe 2288 780 3 69 2015-03-06 09:21:23 UTC+0000
.. 0x83f7f5a0:taskhost.exe 3308 464 5 91 2015-03-06 09:21:28 UTC+0000
.. 0x83e8d930:svchost.exe 300 464 14 329 2015-03-06 08:26:32 UTC+0000
.. 0x85735030:svchost.exe 692 464 20 525 2015-03-06 08:25:10 UTC+0000
... 0x840c9030:audiodg.exe 1072 692 8 144 2015-03-06 08:38:08 UTC+0000
.. 0x841b72b0:taskhost.exe 2884 464 10 163 2015-03-06 09:21:23 UTC+0000
.. 0x85b7c030:svchost.exe 1484 464 16 303 2015-03-06 08:25:26 UTC+0000
.. 0x85b3e630:svchost.exe 1364 464 18 305 2015-03-06 08:25:26 UTC+0000
.. 0x8570cc88:svchost.exe 804 464 28 982 2015-03-06 08:25:11 UTC+0000
.. 0x85b30030:spoolsv.exe 1316 464 13 265 2015-03-06 08:25:26 UTC+0000
.. 0x85a349b8:svchost.exe 1116 464 16 414 2015-03-06 08:25:16 UTC+0000
.. 0x83ebd030:SearchIndexer. 1444 464 14 995 2015-03-06 08:27:29 UTC+0000
... 0x85b40848:SearchFilterHo 2572 1444 5 87 2015-03-06 09:27:49 UTC+0000
... 0x83f59720:SearchProtocol 280 1444 7 240 2015-03-06 09:27:38 UTC+0000
.. 0x8577cc88:svchost.exe 1004 464 18 415 2015-03-06 08:25:14 UTC+0000
.. 0x85c13030:sppsvc.exe 1400 464 5 147 2015-03-06 08:27:29 UTC+0000
.. 0x85757030:svchost.exe 636 464 8 289 2015-03-06 08:25:10 UTC+0000
. 0x859ab5b0:lsass.exe 480 368 7 676 2015-03-06 08:25:06 UTC+0000
. 0x859a8590:lsm.exe 488 368 10 174 2015-03-06 08:25:06 UTC+0000
0x83f82920:explorer.exe 1312 988 20 814 2015-03-06 08:32:47 UTC+0000
. 0x84729030:Solitaire.exe 2992 1312 8 218 2015-03-06 08:43:46 UTC+0000
. 0x8409d688:calc.exe 2192 1312 3 72 2015-03-06 08:42:27 UTC+0000
. 0x85710538:notepad.exe 2964 1312 1 57 2015-03-06 08:43:38 UTC+0000
. 0x8418a030:firefox.exe 2584 1312 51 580 2015-03-06 08:42:38 UTC+0000
. 0x84004540:jusched.exe 376 1312 4 195 2015-03-06 08:32:48 UTC+0000
.. 0x83fbc8c8:jucheck.exe 1280 376 5 217 2015-03-06 08:37:49 UTC+0000
. 0x84033030:iexplore.exe 1088 1312 10 368 2015-03-06 08:42:00 UTC+0000
.. 0x841dba88:iexplore.exe 2456 1088 9 258 2015-03-06 08:49:00 UTC+0000
.. 0x84126340:iexplore.exe 3916 1088 0 ------ 2015-03-06 08:46:45 UTC+0000
... 0x83e4ed40:notepad.exe 4088 3916 4 144 2015-03-06 08:47:29 UTC+0000
.... 0x83e6dac8:iexplore.exe 3468 4088 1 7 2015-03-06 09:13:16 UTC+0000
.. 0x85ad8928:iexplore.exe 2144 1088 10 283 2015-03-06 08:51:08 UTC+0000
. 0x8408d220:wmplayer.exe 3148 1312 23 577 2015-03-06 08:44:00 UTC+0000
. 0x84006938:StikyNot.exe 2000 1312 8 129 2015-03-06 08:32:48 UTC+0000
0x83d33bb0:System 4 0 81 685 2015-03-06 08:24:52 UTC+0000
. 0x84c748f8:smss.exe 248 4 2 32 2015-03-06 08:24:52 UTC+0000
0x858682b8:winlogon.exe 420 360 3 108 2015-03-06 08:25:04 UTC+0000
0x8584ed40:csrss.exe 380 360 7 348 2015-03-06 08:25:04 UTC+0000
. 0x83e85a80:conhost.exe 3392 380 1 32 2015-03-06 09:13:16 UTC+0000
0x85cba2b8:csrss.exe 2472 796 7 154 2015-03-06 09:21:07 UTC+0000
0x841e3030:winlogon.exe 2012 796 5 113 2015-03-06 09:21:07 UTC+0000
0x84af2950:explorer.exe 2232 2296 21 626 2015-03-06 09:21:23 UTC+0000
. 0x840c5550:jusched.exe 3232 2232 6 137 2015-03-06 09:21:25 UTC+0000
There was plenty of things running, but something caught my eye:
Name Pid PPid Thds Hnds Time
-------------------------------------------------- ------ ------ ------ ------ ----
. 0x84033030:iexplore.exe 1088 1312 10 368 2015-03-06 08:42:00 UTC+0000
.. 0x841dba88:iexplore.exe 2456 1088 9 258 2015-03-06 08:49:00 UTC+0000
.. 0x84126340:iexplore.exe 3916 1088 0 ------ 2015-03-06 08:46:45 UTC+0000
... 0x83e4ed40:notepad.exe 4088 3916 4 144 2015-03-06 08:47:29 UTC+0000
.... 0x83e6dac8:iexplore.exe 3468 4088 1 7 2015-03-06 09:13:16 UTC+0000
Internet Explorer using PID 1088
`- lauched a new process (probably a new window) using PID 2456
`- lauched a new process using PID 3916
… so far nothing suspicious
Then a Notepad is lauched (it could be a text file downloaded and the user clicked on “Open”) but Notepad can’t lauch a new process.
Metasploit is using “notepad.exe” as default process name to spawn and inject its payload into memory.
We can thus deduce that the iexplore.exe using PID 3468 lauched by notepad.exe is very suspicious.
It’s time to dump it :
$ python vol.py -f dump --profile=Win7SP1x86 procdump -p 3468 -D files
We loaded “executable.3468.exe” into IDA, lauched the debugger and few breakpoints after we saw a gethostbyname function.
This function is used to get the IP address using a DNS resolve, in our case if the resolve fails then the executable exits.
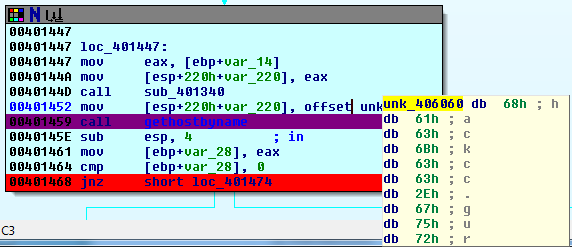
So we modified our host file with hackcc.guru matching 127.0.0.1 and relauched the debugger.
Using TCPView (part of Sysinternal Suite), we saw an outgoing connection on hackcc.guru:4162/tcp
Flag is “hackcc.guru:4162“.
 [HackingWeek 2015] [Forensic 4] Write Up
[HackingWeek 2015] [Forensic 4] Write Up