Description
We need your investigation skills on the siem2* Kibana index. The attack occured in 2018, it is reccommended to set your timeline prior to this year.
ELK/Kibana via web-service
SIEM Logs Challenge: Flag Identification through Regex Detection
This challenge focuses on analyzing SIEM (Security Information and Event Management) logs to extract specific information and identify potential threats through the use of regular expressions (regex). The goal is to capture data such as the IP address, hostnames, and suspicious WordPress login attempts.
Steps for Solving the Challenge
1. Analyzing the Logs
We were given logs that detail HTTP POST requests to WordPress login pages. These logs provide information such as:
- Source IP Address
- Destination IP Address
- User Agent
- Payload Data (including WordPress cookies)
A notable feature in these logs is the wordpress_test_cookie, which is used during WordPress logins to verify if the client browser accepts cookies. The presence of this cookie in repeated login attempts could suggest automated or malicious activity.
2. Regex for Detection
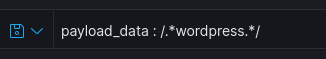
To detect these WordPress login attempts, we used a regex to search for occurrences of the term wordpress in the logs. The regex used was:
/.*wordpress.*/This regex captures any log entry containing the word wordpress, specifically focusing on login attempts that use WordPress-related cookies.
3. Extracting the Flags
Based on the analysis of the logs, the following flags were identified for each question:
- Q1: Destination IP Address
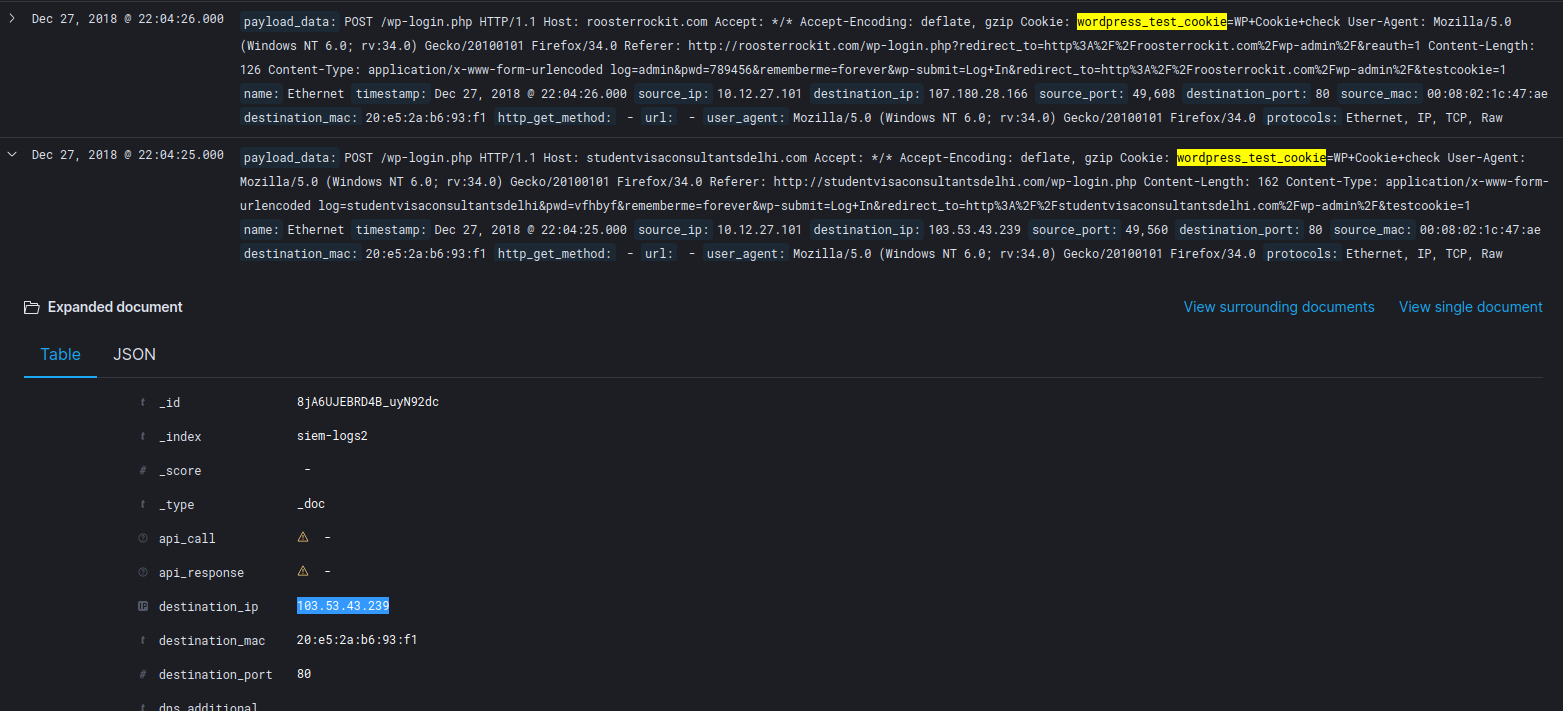
The first question asks for the destination IP address, which is clearly displayed in the logs:
destination_ip: 103.53.43.239- Flag Q1:
103.53.43.239 - Q2: Hostname
The second question requests the hostname involved in one of the login attempts. This can be seen in the payload data:
Host: studentvisaconsultantsdelhi.com- Flag Q2:
studentvisaconsultantsdelhi - Q3: WordPress Cookie (Flag)
The third question is based on detecting the wordpress_test_cookie, indicating a login attempt on a WordPress site. The presence of this cookie in the log data allows us to identify the flag:
Cookie: wordpress_test_cookie=...- Flag Q3:
wordpress
4. Sample Log Entries
Here are two sample log entries analyzed during this challenge:
- Log Entry 1:
Dec 27, 2018 @ 22:04:26.000
payload_data: POST /wp-login.php HTTP/1.1 Host: roosterrockit.com Accept: */* Cookie: wordpress_test_cookie=...
source_ip: 10.12.27.101
destination_ip: 107.180.28.166
source_port: 49,608
destination_port: 80- Log Entry 2:
Dec 27, 2018 @ 22:04:25.000
payload_data: POST /wp-login.php HTTP/1.1 Host: studentvisaconsultantsdelhi.com Cookie: wordpress_test_cookie=...
source_ip: 10.12.27.101
destination_ip: 103.53.43.239
source_port: 49,560
destination_port: 80Conclusion
Through regex detection and analysis of the SIEM logs, we identified important information such as the destination IP, hostname, and the presence of a suspicious WordPress cookie, which helped us capture the flags for each question.
Flags Recap:
- Flag Q1:
103.53.43.239 - Flag Q2:
studentvisaconsultantsdelhi - Flag Q3:
wordpress
This write-up details the steps taken to solve the SIEM logs challenge and capture the necessary flags.
 [Defcamp Quals 2024] [Threat Intel – SIEM-LOGS] WRITE UP
[Defcamp Quals 2024] [Threat Intel – SIEM-LOGS] WRITE UP