Description
Sniffing traffic is fun. I saw a wired shark. Isn’t that strange?
Resolution
There was only 3 HTTP GET requests (packets #13 and #37).
The response to the 1st HTTP GET request (packet #29) was a 401 Unauthorized.
The response to the 2nd HTTP GET request (packet #53) was a HTML page:
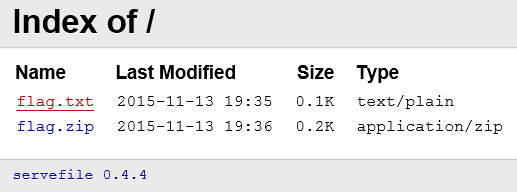
Based on the GET request (packet #37), we noticed the access was allowed due to a good AUTH header:
Authorization: Basic ZmxhZzphenVsY3JlbWE=
(Plaintext credentials: flag:azulcrema)
The 3rd HTTP request (packet #61), was a downloading of “flag.zip”.
We dumped the file but there was a password so we tried “azulcrema” and it worked to get a flag.txt.
Flag was IW{HTTP_BASIC_AUTH_IS_EASY}
 [Internetwache CTF 2016] [Misc 70 – Rock with the wired shark!] Write Up
[Internetwache CTF 2016] [Misc 70 – Rock with the wired shark!] Write Up